Hollows_Hunter
0.3.0Scan the visible and hidden running process on your system and find out whether you are dealing with malicious implants using this tool
With new malware being developed every day, it doesn't come as a surprise that it can take multiple forms and make its way even to advanced users' computers. This is why keeping an eye out for suspicious processing or those running in the background and eating a lot of the PC's resources cannot be stressed enough.
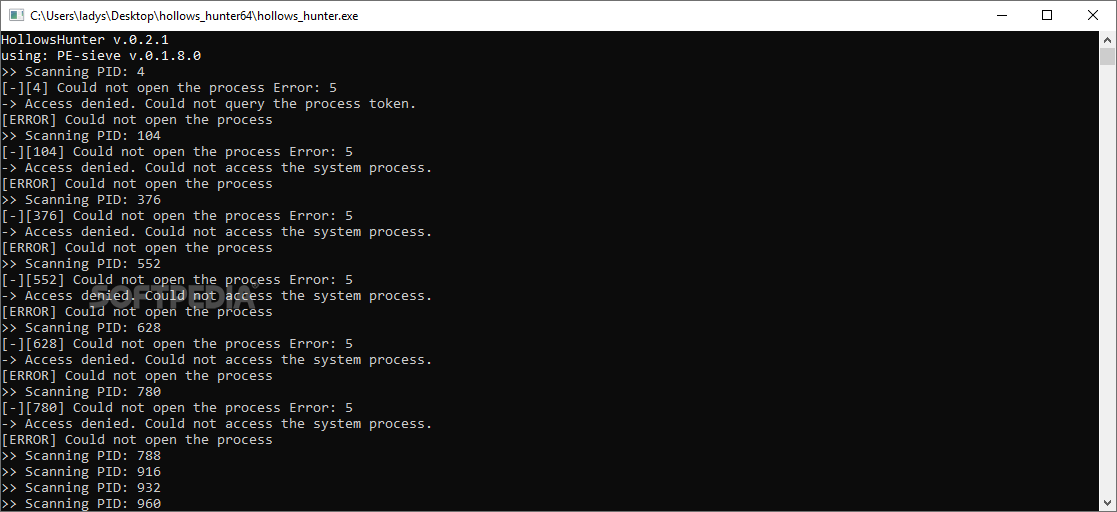
Hollows_Hunter is a tiny tool designed to help you scan the running processes and identify anything suspicious or out of the ordinary, such as in memory modifications or unauthorized changes.
The program can be run standard or in command line, but it is mandatory that you use an Administrator Account. Since the idea behind the tool is to scan running processes, both visible and hidden, it means it needs to access various folders that can only be accessed with Admin rights.
As previously mentioned, the idea here is to help you recognize and manage various suspicious implants, including but not limited to hooks, in-memory patches, shellcodes or replaced as well as implanted PEs. For this purpose, it relies on PE-Sieve, a tool designed to help you scab active PE processes to detect in-memory code modifications.
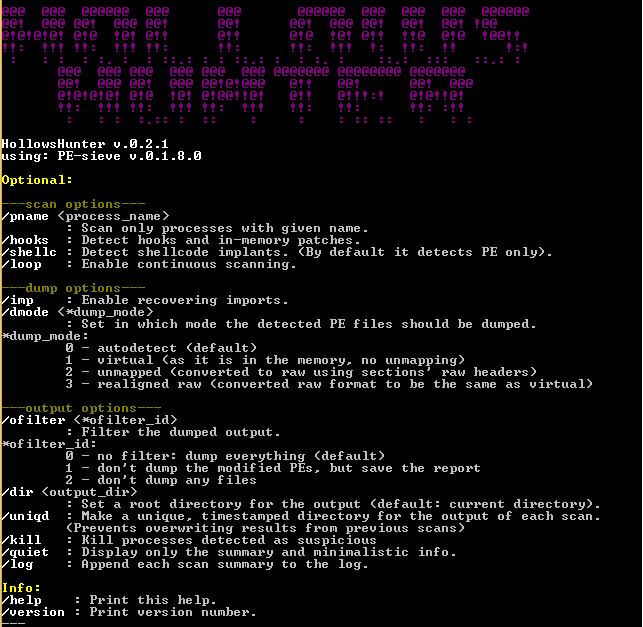
It is worth mentioning that the app can be run with parameters that allow you to scan for a particular process or a directory. Moreover, you can scan continuously, in case you are trying to test a potentially malicious code.
At the same time, the program can enable the recovery imports or the dump mode, in which the PE files are essentially dumped. It goes without saying that you can kill the processes detected as suspicious and determine whether they pop up again when running a particular app, for instance.
Hollows_Hunter is a tool that addresses advanced users and that provides them with a specialized tool capable of detecting an impressive array of potentially malicious implants.
Hollows_Hunter is a tiny tool designed to help you scan the running processes and identify anything suspicious or out of the ordinary, such as in memory modifications or unauthorized changes.
It can detect in-memory patches, implanted PEs and shellcodes
The program can be run standard or in command line, but it is mandatory that you use an Administrator Account. Since the idea behind the tool is to scan running processes, both visible and hidden, it means it needs to access various folders that can only be accessed with Admin rights.
As previously mentioned, the idea here is to help you recognize and manage various suspicious implants, including but not limited to hooks, in-memory patches, shellcodes or replaced as well as implanted PEs. For this purpose, it relies on PE-Sieve, a tool designed to help you scab active PE processes to detect in-memory code modifications.
An advanced tool that can help protect your system from the latest malware
It is worth mentioning that the app can be run with parameters that allow you to scan for a particular process or a directory. Moreover, you can scan continuously, in case you are trying to test a potentially malicious code.
At the same time, the program can enable the recovery imports or the dump mode, in which the PE files are essentially dumped. It goes without saying that you can kill the processes detected as suspicious and determine whether they pop up again when running a particular app, for instance.
Hollows_Hunter is a tool that addresses advanced users and that provides them with a specialized tool capable of detecting an impressive array of potentially malicious implants.
748 KB
Info
Update Date
Aug 10 2021
Version
0.3.0
License
BSD License
Created By
hasherezade
Related software Security

DeviceLock
9.0.91972
1.8 GB

iWatermark Pro
2.5.30
222 MB

Hotspot Shield
10.18.1 / 2.10.4.0 Store App
20.8 MB

Advanced Identity Protector
2.2.1000.2715
9.8 MB

Password Manager XP Professional
4.0 Build 812
3.6 MB

WashAndGo
22 (26.46)
26.9 MB

Elcomsoft Distributed Password Recovery
4.41 Build 1555
246 MB