Advanced Identity Protector
2.2.1000.2715A smart and effective way to keep user identity secure from unauthorized access, in order to prevent identity theft and online scammers.
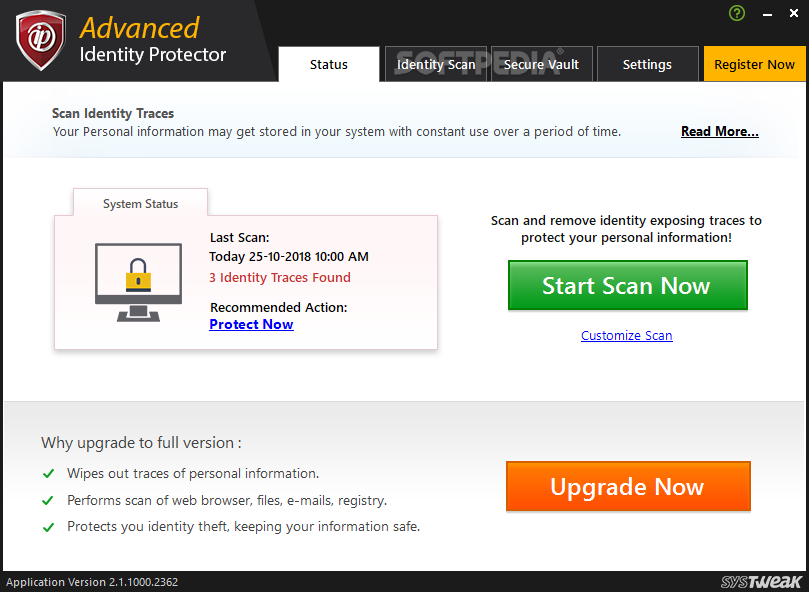
Advanced Identity Protector is an efficient application that digs up personal information from various environments and displays it to you. You can then choose to delete, store them in a safe place or mark them as exclusions. This way, your system will be free of potential material for identity thieves.
The Secure Vault is an internal feature that lets you store sensible information under an encrypted format. Also, the vault can only be accessed by providing a password, so if you want to be the only one accessing it, don't share the password. THe vault can also be operated automatically, in relation with the Delete, Move to Secure Vault or Exclude commands.
Furthermore, you can choose to permanently delete the info traces from your system, in order to maximize the identity theft protection or you can exclude them if you deem them harmless. The excluded traces are not going to be displayed in the scan results.
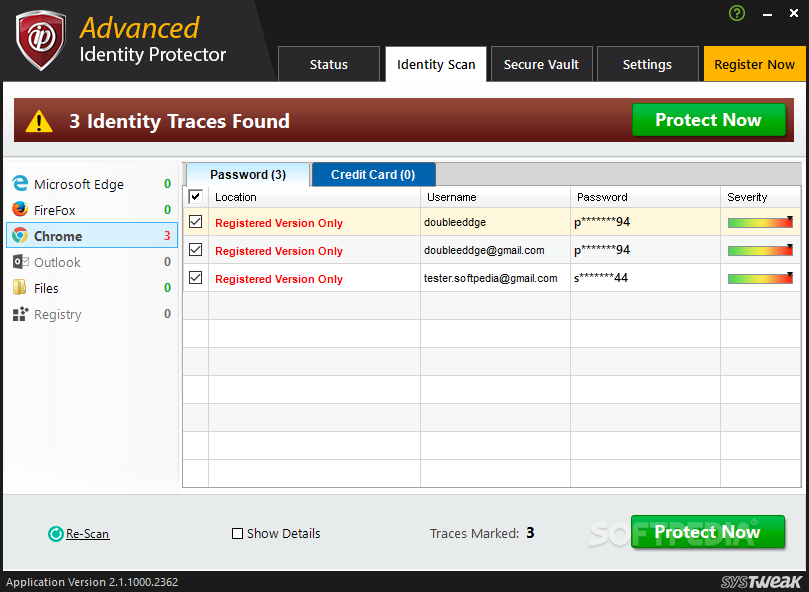
Advanced Identity Protector can scan for information leftovers in your browsers, mail clients and system files. Regarding the mail clients, only Outlook and Outlook Express are supported The main supported browsers are Internet Explorer, Firefox and Chrome; these are the standard scans. If you need to keep a browser out of the scanning process, simply uncheck the boxes near the title, and it's done.
An interesting an useful feature regarding the browser scan is that you can reveal the names and passwords for logged accounts. This makes for a great account recovery process as it's very simple to use.
To sum it up, Advanced Identity Protector is a smart and straightforward tool that can boost your online protection by allowing you to manage your information traces. It can scan the different web and system environments and provide you all info leftovers you left behind. From there it gives you total access to process them as you need.
Secure or exclude private information
The Secure Vault is an internal feature that lets you store sensible information under an encrypted format. Also, the vault can only be accessed by providing a password, so if you want to be the only one accessing it, don't share the password. THe vault can also be operated automatically, in relation with the Delete, Move to Secure Vault or Exclude commands.
Furthermore, you can choose to permanently delete the info traces from your system, in order to maximize the identity theft protection or you can exclude them if you deem them harmless. The excluded traces are not going to be displayed in the scan results.
Supported Environments
Advanced Identity Protector can scan for information leftovers in your browsers, mail clients and system files. Regarding the mail clients, only Outlook and Outlook Express are supported The main supported browsers are Internet Explorer, Firefox and Chrome; these are the standard scans. If you need to keep a browser out of the scanning process, simply uncheck the boxes near the title, and it's done.
An interesting an useful feature regarding the browser scan is that you can reveal the names and passwords for logged accounts. This makes for a great account recovery process as it's very simple to use.
Handy information tracker
To sum it up, Advanced Identity Protector is a smart and straightforward tool that can boost your online protection by allowing you to manage your information traces. It can scan the different web and system environments and provide you all info leftovers you left behind. From there it gives you total access to process them as you need.
9.8 MB
Info
Update Date
Apr 30 2021
Version
2.2.1000.2715
License
Demo
Created By
Systweak Inc
Related software Security